A crisis like COVID-19 is ideal breeding ground for cyber-attackers preying on general fears and misinformation. Since the pandemic began, several government and global organizations, including the Centers for Disease Control and Prevention (CDC), have reported an increase in phishing emails.
A crisis like COVID-19 is ideal breeding ground for cyber-attackers preying on general fears and misinformation. Since the pandemic began, several government and global organizations, including the Centers for Disease Control and Prevention (CDC), have reported an increase in phishing emails.
“Phishing” is the most common type of cyber-attack that affects organizations like ours. Phishing attacks can take many forms, but they all share a common goal – getting you to share sensitive information such as login credentials, credit card information, or bank account details.
Although we maintain strict controls to help protect our networks and computers from cyber threats, we rely on you to be our first line of defense. You can do that by following good cyber-hygiene practices such as those listed below:
- Do not click on links or attachments from senders that you do not recognize. Be especially wary of .zip or other compressed or executable file types.
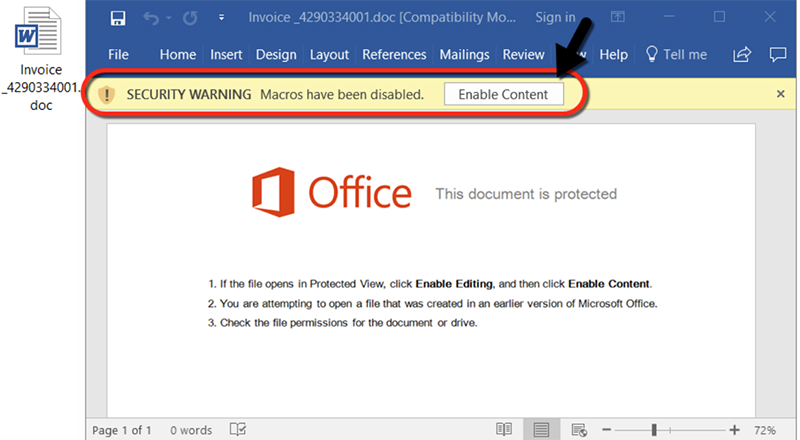
- Be wary of any email that asks you to open a document and run a macro. If you open a document and see a similar message to the one circled below, do not click on “Enable Content” unless you are specifically expecting such a document.
- Never open any shared document that you’re not expecting to receive.
- Inspect URLs embedded in email messages carefully to make sure they’re legitimate and not imposter sites.
- Do not provide sensitive personal information (like usernames and passwords or financial information) over email.
- Watch for email senders that use suspicious or misleading domain names.
- Be cautious about emails where you can’t tell if an email is legitimate or not such as:
- If it comes from an unexpected or unknown sender
- If it comes from a sender you know, but whose email address doesn’t match their actual email address
- If the sender appears to be someone you know, but they “sound” different, or request that you do something out of the ordinary
- Be suspicious of emails that imply some dire consequence if you don’t follow the instructions such as your email account will be disabled, you won’t receive a paycheck, retribution from a government agency, etc.
- Be wary of emails that have the [External] tag in the subject, especially if they appear to come from someone at Emory. The [External] tag means that the message was not sent from someone with an Emory email account.
- Uses generic salutations and signatures.
Non-email cyber-safety reminders
- Use an Emory owned and managed computer for your work whenever possible.
- Choose a password for your Emory account that is unique and not used anywhere else. Hackers will use a compromised password from one website or organization to try and compromise additional accounts by using that same password. Sharing passwords across accounts puts you at risk.
- Pay attention whenever you get a notification from Duo to approve a login. Did you just attempt to login to your account immediately prior to receiving the notification? If not, deny the request. It could be a sign that someone is attempting to use your current password to login.
- If you think your password has been compromised, change it immediately by going to https://mypassword.emory.edu:8443/sspr.
- Speak with your IT support staff to ensure any sensitive or confidential research data is stored on Emory’s “Trusted Storage” service, or on Emory’s Box.com or OneDrive storage services.
- Do not leave devices unattended in public locations, and never leave devices in a vehicle under any circumstances.
For those in our essential research labs, please pay attention to the following specific examples related to COVID-19
- Be aware of phishing emails asking you to verify your personal information to receive an economic stimulus check from the government. Government agencies are not sending unsolicited emails seeking your private information in order to send you money.
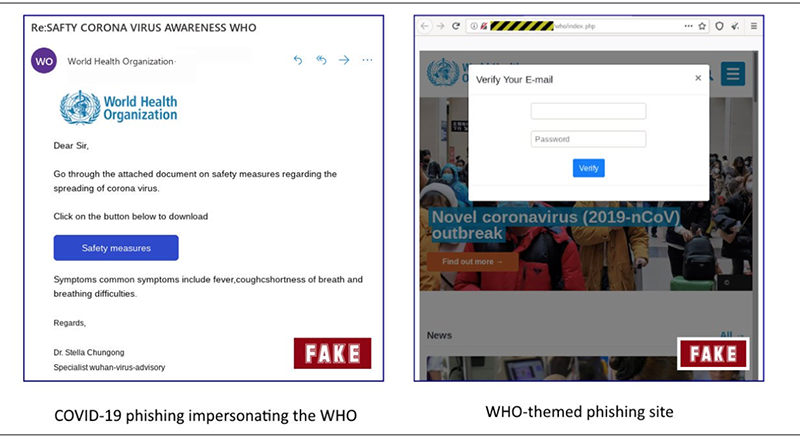
- Watch out for emails claiming to be from the CDC or the World Health Organization, or other organizations pretending to offer information on the virus.
- Fraudsters can use links in such emails to deliver malware to your computer to steal personal information or to lock your computer and demand payment. Practice extreme caution when clicking on links or attachments. Hover your mouse over a link to see where it’s sending you.
- Be wary of websites and apps claiming to track COVID-19 cases worldwide. Criminals are using malicious websites to infect and lock devices until payment is received.
- Be cautious of anyone selling products that claim to prevent, treat, diagnose, or cure COVID-19. Be alert to counterfeit products such as sanitizing products and Personal Protective Equipment (PPE), including N95 respirator masks, goggles, full face shields, protective gowns, and gloves.